 I just finished reading the book Intelligent Automation by Pascal Bornet. It’s a fascinating look at the future implementation of artificial intelligence in today’s and future businesses. Since my role is to assess and understand the cybersecurity threats on the maritime sector, Bornet’s book caused me to look for analysis and resources regarding autonomous ships and their implementation.
I just finished reading the book Intelligent Automation by Pascal Bornet. It’s a fascinating look at the future implementation of artificial intelligence in today’s and future businesses. Since my role is to assess and understand the cybersecurity threats on the maritime sector, Bornet’s book caused me to look for analysis and resources regarding autonomous ships and their implementation.
I was surprised at how much has been written on this subject. As an experiment, I suggest you do a Google search on terms such as “autonomous ships,” “autonomous seaports,” etc. I think you’ll be surprised.
What I’d like to provide in this article is a brief survey of autonomous ships and offer some thoughts on the cybersecurity risks that should be considered before fully autonomous operations are implemented.
What is Artificial Intelligence?
The idea of autonomous ships is not new. Autonomous ships are vessels capable of navigating and operating without the need for human intervention. Such ships use technologies including cameras, sensors, Global Positioning Systems (GPS) and artificial intelligence (AI).
AI integrates processes that include learning, reasoning and self-correction. It uses techniques and technologies such as machine learning, sentiment analysis, data management platforms, speech analytics, data visualization, image and video analysis, biometrics, intelligent chatbots, smart workflows, low-code platforms, robotic process automation (RPA) and natural language processing.
To simplify this list, you can look at AI as incorporating the following capabilities:
- Vision – e.g., optical character recognition (OCR)
- Execution – e.g., the actual “doing”
- Language – e.g., intelligent chat bots, speech analytics, and
- Thinking and learning – e.g., machine learning, data visualization, etc.
These capabilities have exciting opportunities in the immediate and long-term future. However, a key foundation to all the technologies is reliance on cyber systems, software, firmware and hardware. These can all be attacked or modified by a skilled adversary.
Hence, considerations for cybersecurity should be incorporated into the early design and implementation of autonomous ships and seaports.
What is an Autonomous Ship?
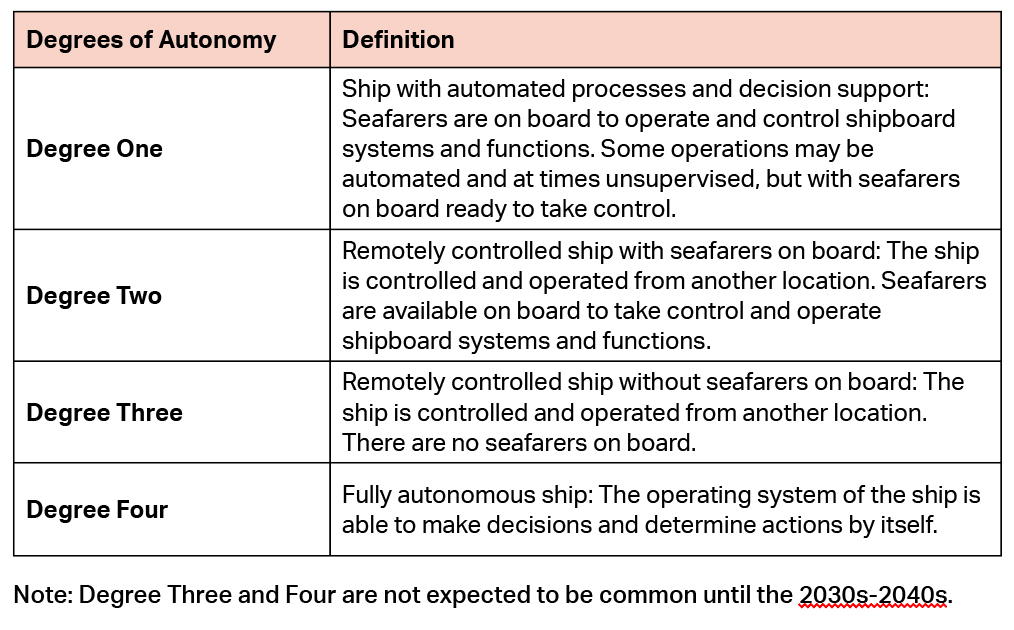
The International Maritime Organization (IMO) has devoted substantial time addressing autonomous ships and their impact on the global maritime environment. The IMO refers to autonomous ships by the term “MASS,” which stands for Maritime Autonomous Surface Ships. Per IMO, MASS is defined as “…a ship which, to a varying degree, can operate independent of human interaction.” (MSC.1/Circ. 1638)
The IMO has addressed the different degrees of ship autonomy and categorized them as follows from minimally to fully autonomous.
How Important is MASS?
In its November 2020 Maritime Autonomy Regulation Lab (MARLab) report, the United Kingdom’s government said MASS is worth $1.1 billion annually and expected to rise almost 7% by 2025. MASS technology has received more than $113 million in venture capital since 2010. China is forecast to be a world leader in MASS technology by 2025.
Maersk and IBM have been integrating AI systems into ship operations, and in 2018 China began construction of the world’s biggest test site for unmanned vessels in the port of Zhuhai.
The U.S. Navy and the UK Royal Navy have implemented autonomous systems in some naval vessels.
In Norway there’s a collaboration between a fertilizer company—YARA—and Kongsberg—a maritime engineering company. The vessel, Yara Birkeland, is a fully electric and autonomous container ship with zero emissions. The ship is a 120 TEU (twenty-foot equivalent units) open-top container ship.
The vessel is equipped with an automatic mooring system thus requiring minimal human intervention. In 2022, it commenced commercial operations in Norwegian waters with the first set of highly automated systems and an onboard crew. Commercial operation as an uncrewed vessel with autonomous capabilities is anticipated by 2024.
 Benefits of MASS
Benefits of MASS
As with any opportunity to automate systems and equipment there are perceived benefits. Some industry analysts view autonomous ships as helping with the following:
- Minimizing or eliminating human error
- Optimizing ship routing and navigation
- Reducing costs associated with assigned onboard crews
- Reducing ship weight by reducing the size of the ship’s superstructures
- Reducing construction costs
- Improving safety
- Allowing for more efficient use of space in ship design
- Increasing cargo capacity,
- Improving fuel use and emissions management, and
- Increasing competitiveness in the maritime industry.
Risks of Autonomous Ship Operations
Full automation is not without risks, however. Even if you look at the history of some “fully automated automobiles” there have been tragic, fatal accidents.
Some of the risks to consider when operating MASS include collisions, environmental spills and disasters, fires, hazardous materials events, severe weather conditions, hijacking or extortion, cargo theft and cybersecurity threats.
One concern about AI and autonomous operations is the human factor—that is, resistance to change since adoption of autonomous technology may be viewed as a threat to their livelihoods.
As a consideration, the level of autonomy of the ship will be proportional to the cyberattack surface since the attack surface varies with the complexity and dependency of the automated systems. Thus, the more autonomous, the more complex and the larger a target for cyberattacks.
Chris South, senior underwriter for insurance provider West of England P&I, has observed four factors driving maritime cybersecurity. They are:
- Automation—machinery and operating systems are increasingly controlled by software
- Integration—multiple shipboard systems are interconnected
- Remote monitoring—corporate land-based offices use ship-to-shore communications to continuously monitor shipboard equipment, and
- All these systems are connected to the Internet.
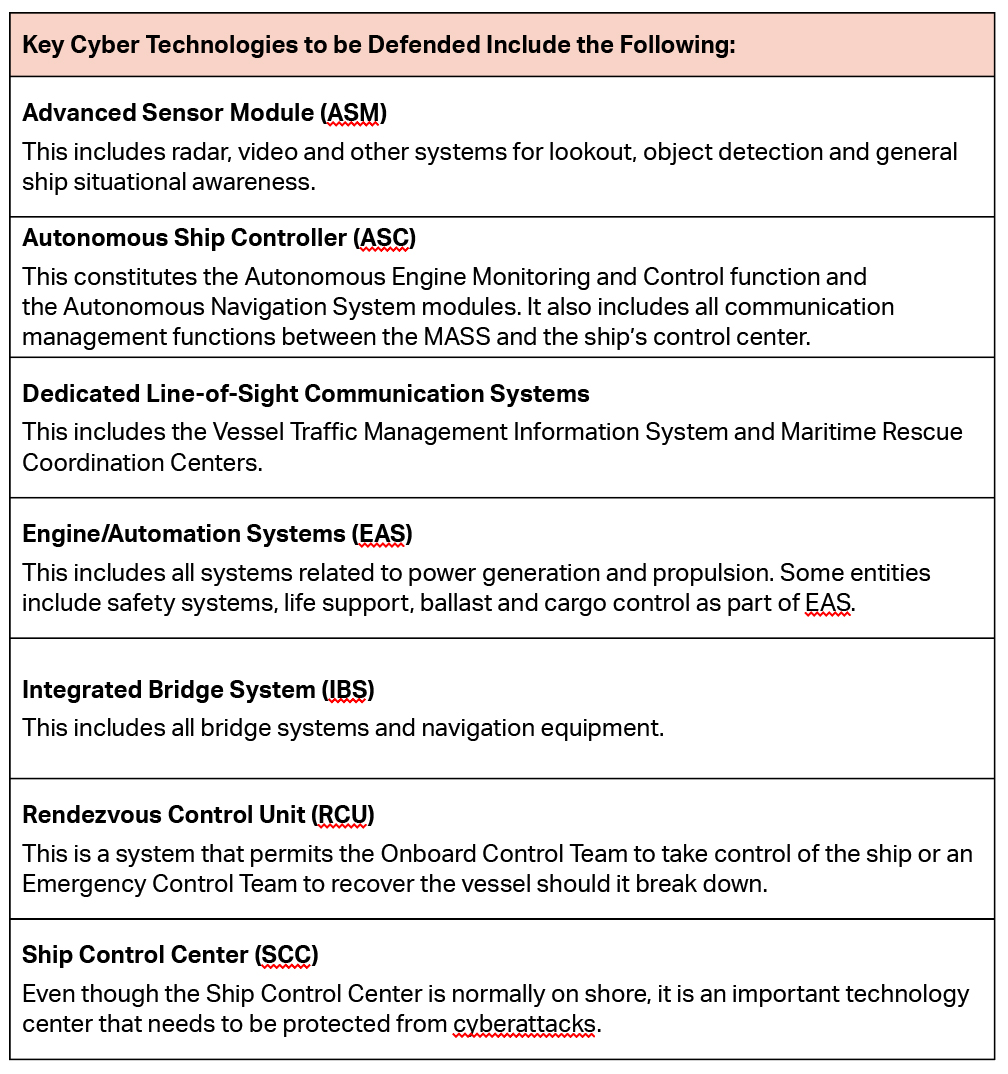
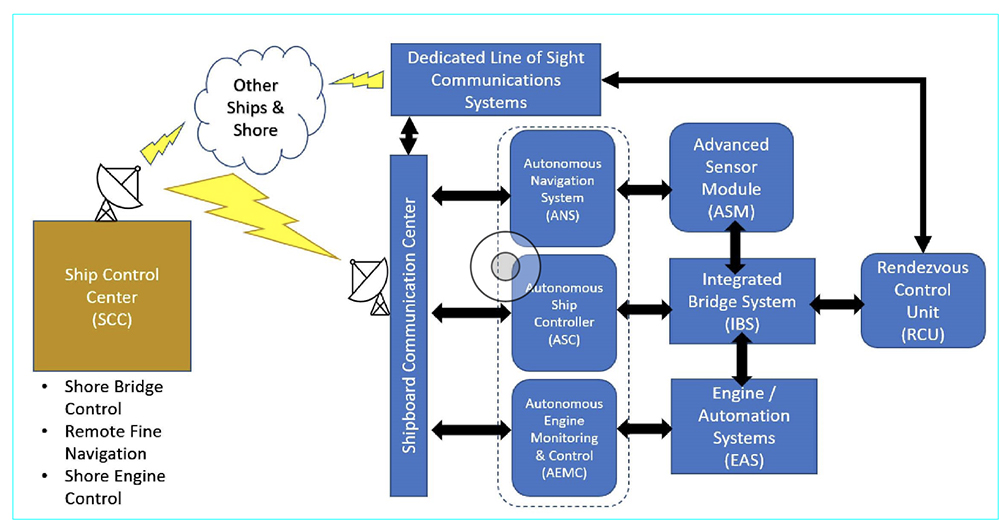
In theory, any cyber system can be “hacked” and either made inoperative or taken over by the attacker (an elementary block diagram of the MASS control modules is shown above).
Since these are electronic technologies, there are nine categories of threats that may be specific to autonomous ships. They are identified in the document Cybersecurity Considerations in Autonomous Ships by the NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE) and include:
- Disruption of RF signals.
- Deception or degradation of sensors
- Interception or modification of communications streams
- Attacks on operational technology (OT) systems
- Attacks on information technology (IT) systems
- Cyber assaults on AI used for autonomous operations
- Cyber integrity violations through supply chains
- Attacks through physical access, and
- Attacks on the shore control center.
These attacks and disruptions may be executed via:
- Malicious code injection by network infiltration
- Removable devices (e.g., plugging in contaminated USB drives)
- Faulty or malicious firmware updates
- Tampering or modification of intra-vessel network packets
- GNSS spoofing
- AIS spoofing
- Signal jamming against GNSS and other sensors, and
- Eavesdropping and disruption of the communication link between the vessel and shore control center.
The attacks may be specific to a particular control module or across multiple control systems. As such, they are not easily defended without substantial work and constant oversight.
A Call to Action
Since the MASS technologies are early in their implementation, it is best that a strong, multi-level cyber-risk management approach be taken. This action would include threat modeling and identification of necessary countermeasures to reduce and preferably eliminate the impact of cyber-attacks.
Therefore, security needs to be taken into account long before the keel is laid. The security considerations need to be applied from the beginning of the planning and design stage rather than taking corrective action long after the MASS has left the pier.
If you have any comments or questions on this article or on maritime cybersecurity issues, the author, Ernie Hayden, can be reached via ernie@erniehayden.com.
Ernie Hayden, MIPM CISSP GICSP (Gold) PSP, is an industrial control systems cyber and physical security subject matter expert. He has extensive experience in industrial controls security, the power utility industry, critical infrastructure protection/information security, cybercrime and cyberwarfare. His email is ernie@erniehayden.com.

